前書き
前回、Catalyst 8000vでvlan-awareのEVPN-VXLANを検証しましたが、SVIの設定ができなかったことが原因で集中型GWのIRBは未実装でした。
集中型ができないならということで、今回は分散型Anycast-GatewayのIRBに挑戦します。
環境
CMLをProxmoxVE上に立てて環境構築しています。
- CML2.7
次に各ノードの紹介です。
- Catalyst 8000v ×3(以降cat8000v)
- IOSv ×4(以降iosv)
構成図
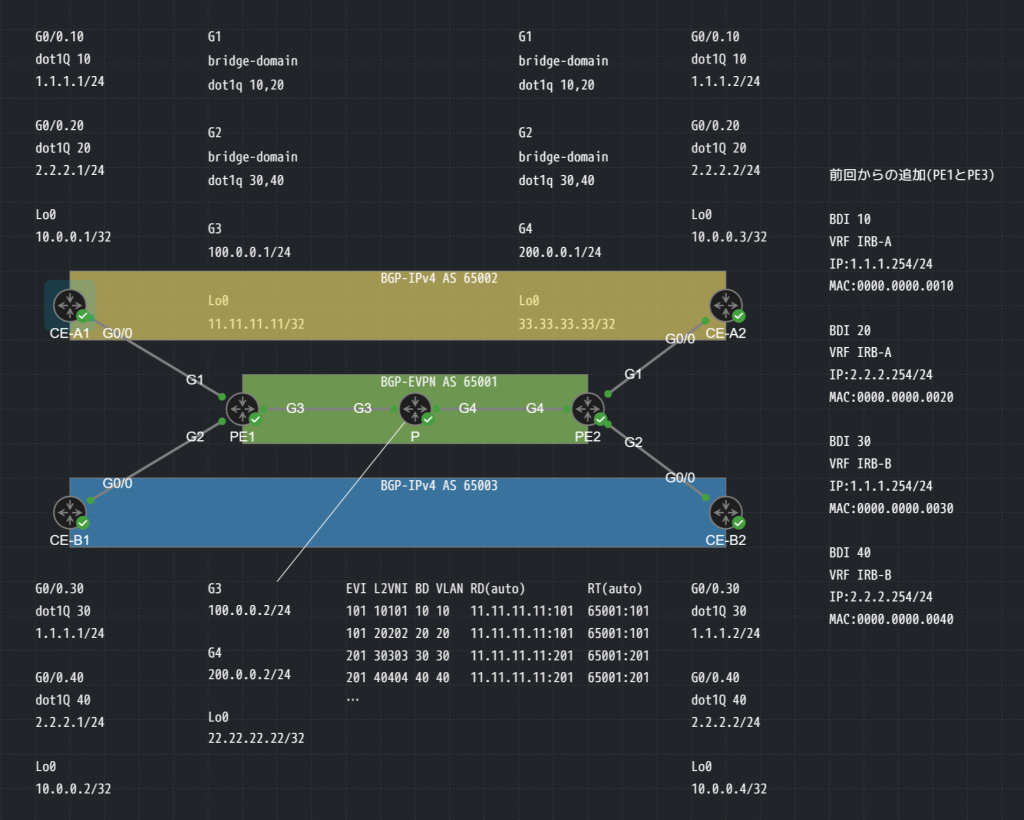
前回同様、緑色が回線事業者想定で、黄色がA社、青色がB社としたときにA社とB社は互いにルーティングはできず、同じIPv4アドレスを一部重複して持っているというシナリオです。
今回もvlan-aware1の方式を使っているため、1つのVLANが1つのBD(bridge-domain)と1つVNIに紐づき、N個のBDが1つのEVIに紐づいています。今回はIRB(L3VNI)の構築ができなかったので、A社のルータは対向のA社のルータと直接ピアを結んでいます。
図は前回とほぼ同じですがIRBを追加する上でcat8000vにBDIを追加し、IPv4 VRFで分けました。
BDIはBDと紐づき、今回の場合はほぼVLANとイコールなので1つのEVIに2つのBDIがぶら下がっており、このBDIは2つで1つのVRFに紐づいています。
関係性が複雑になってきたので、図で表すとこんなイメージでしょうか。(間違ってたらすみません、特にL3VNI)
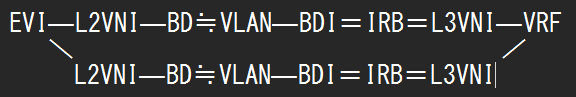
分散型Anycast-Gatewayを実現するためにはPE1とPE2の同一BDIのIPアドレスとMACアドレスを同じにする必要があり、その方法としてCiscoでは二つ方法が紹介されています。2
- MACアドレスの手動登録
- MACエイリアシング
自分が調べた限りIOS-XEではMACエイリアシングのコンフィグはなさそうなので今回は手動設定しています。3
コンフィグ
予め、cat8000vの4台はライセンスのアドバンテージライセンス有効化済み4の前提です。
前回から変わっているのはPE1とPE2のみです。
PE1
en
!
conf t
!
hostname pe1
!
ip routing
!
vrf definition IRB-A
rd 65002:1
address-family ipv4 unicast
!
vrf definition IRB-B
rd 65003:1
address-family ipv4 unicast
!
interface Loopback 0
ip address 11.11.11.11 255.255.255.255
ip ospf 1 area 0
!
interface GigabitEthernet 1
no shutdown
no ip address
negotiation auto
service instance 10 ethernet
encapsulation dot1q 10
rewrite ingress tag pop 1 symmetric ←CEから来たタグ付きフレームのタグを取る設定です。
service instance 20 ethernet
encapsulation dot1q 20
rewrite ingress tag pop 1 symmetric ←CEから来たタグ付きフレームのタグを取る設定です。
!
interface GigabitEthernet 2
no shutdown
no ip address
negotiation auto
service instance 30 ethernet
encapsulation dot1q 30
rewrite ingress tag pop 1 symmetric ←CEから来たタグ付きフレームのタグを取る設定です。
service instance 40 ethernet
encapsulation dot1q 40
rewrite ingress tag pop 1 symmetric ←CEから来たタグ付きフレームのタグを取る設定です。
!
interface GigabitEthernet 3
ip address 100.0.0.1 255.255.255.0
ip ospf network point-to-point
ip ospf 1 area 0
no shutdown
!
interface bdi 10
vrf forwarding IRB-A
ip address 1.1.1.254 255.255.255.0
mac-address 0000.0000.0010 ←MACアドレスの手動登録
no shutdown
!
interface bdi 20
vrf forwarding IRB-A
ip address 2.2.2.254 255.255.255.0
mac-address 0000.0000.0020 ←MACアドレスの手動登録
no shutdown
!
interface bdi 30
vrf forwarding IRB-B
ip address 1.1.1.254 255.255.255.0
mac-address 0000.0000.0030 ←MACアドレスの手動登録
no shutdown
!
interface bdi 40
vrf forwarding IRB-B
ip address 2.2.2.254 255.255.255.0
mac-address 0000.0000.0040 ←MACアドレスの手動登録
no shutdown
!
router ospf 1
router-id 11.11.11.11
!
router bgp 65001
bgp log-neighbor-changes
no bgp default ipv4-unicast
bgp router-id 11.11.11.11
neighbor 22.22.22.22 remote-as 65001
neighbor 22.22.22.22 update-source Loopback0
!
address-family ipv4
exit-address-family
!
address-family l2vpn evpn
neighbor 22.22.22.22 activate
neighbor 22.22.22.22 send-community both
exit-address-family
!
exit
!
l2vpn evpn
replication-type ingress
router-id loopback 0
default-gateway advertise ←L2VPNのデフォルトGW設定
!
l2vpn evpn instance 101 vlan-aware
encapsulation vxlan
!
l2vpn evpn instance 201 vlan-aware
encapsulation vxlan
!
interface nve1
no ip address
source-interface Loopback0
host-reachability protocol bgp
member vni 10101 ingress-replication
member vni 20202 ingress-replication
member vni 30303 ingress-replication
member vni 40404 ingress-replication
!
bridge-domain 10
mac aging-time 30
member evpn-instance 101 vni 10101
member GigabitEthernet1 service-instance 10
exit
!
bridge-domain 20
mac aging-time 30
member evpn-instance 101 vni 20202
member GigabitEthernet1 service-instance 20
exit
!
bridge-domain 30
mac aging-time 30
member evpn-instance 201 vni 30303
member GigabitEthernet2 service-instance 30
exit
!
bridge-domain 40
mac aging-time 30
member evpn-instance 201 vni 40404
member GigabitEthernet2 service-instance 40
exit
!
end
!
以下はコメントは省略します。
P
en
!
conf t
!
hostname p
!
ip routing
!
interface Loopback 0
ip address 22.22.22.22 255.255.255.255
ip ospf 1 area 0
!
interface GigabitEthernet 3
ip address 100.0.0.2 255.255.255.0
ip ospf network point-to-point
ip ospf 1 area 0
no shutdown
!
interface GigabitEthernet 4
ip address 200.0.0.2 255.255.255.0
ip ospf network point-to-point
ip ospf 1 area 0
no shutdown
!
router ospf 1
router-id 22.22.22.22
!
router bgp 65001
template peer-policy POLICY
route-reflector-client
send-community extended
exit-peer-policy
!
template peer-session SESSION
remote-as 65001
update-source Loopback0
exit-peer-session
!
bgp log-neighbor-changes
no bgp default ipv4-unicast
bgp router-id 22.22.22.22
neighbor 11.11.11.11 inherit peer-session SESSION
neighbor 33.33.33.33 inherit peer-session SESSION
!
address-family ipv4
exit-address-family
!
address-family l2vpn evpn
neighbor 11.11.11.11 activate
neighbor 11.11.11.11 inherit peer-policy POLICY
neighbor 33.33.33.33 activate
neighbor 33.33.33.33 inherit peer-policy POLICY
exit-address-family
!
end
!PE2
en
!
conf t
!
hostname pe2
!
ip routing
!
vrf definition IRB-A
rd 65002:1
address-family ipv4 unicast
!
vrf definition IRB-B
rd 65003:1
address-family ipv4 unicast
!
interface Loopback 0
ip address 33.33.33.33 255.255.255.255
ip ospf 1 area 0
!
interface GigabitEthernet 1
no shutdown
no ip address
negotiation auto
service instance 10 ethernet
encapsulation dot1q 10
rewrite ingress tag pop 1 symmetric
service instance 20 ethernet
encapsulation dot1q 20
rewrite ingress tag pop 1 symmetric
!
interface GigabitEthernet 2
no shutdown
no ip address
negotiation auto
service instance 30 ethernet
encapsulation dot1q 30
rewrite ingress tag pop 1 symmetric
service instance 40 ethernet
encapsulation dot1q 40
rewrite ingress tag pop 1 symmetric
!
interface GigabitEthernet 4
ip address 200.0.0.1 255.255.255.0
ip ospf network point-to-point
ip ospf 1 area 0
no shutdown
!
interface bdi 10
vrf forwarding IRB-A
ip address 1.1.1.254 255.255.255.0
mac-address 0000.0000.0010
no shutdown
!
interface bdi 20
vrf forwarding IRB-A
ip address 2.2.2.254 255.255.255.0
mac-address 0000.0000.0020
no shutdown
!
interface bdi 30
vrf forwarding IRB-B
ip address 1.1.1.254 255.255.255.0
mac-address 0000.0000.0030
no shutdown
!
interface bdi 40
vrf forwarding IRB-B
ip address 2.2.2.254 255.255.255.0
mac-address 0000.0000.0040
no shutdown
!
router ospf 1
router-id 33.33.33.33
!
router bgp 65001
bgp log-neighbor-changes
no bgp default ipv4-unicast
bgp router-id 33.33.33.33
neighbor 22.22.22.22 remote-as 65001
neighbor 22.22.22.22 update-source Loopback0
!
address-family ipv4
exit-address-family
!
address-family l2vpn evpn
neighbor 22.22.22.22 activate
neighbor 22.22.22.22 send-community both
exit-address-family
!
exit
!
l2vpn evpn
replication-type ingress
router-id loopback 0
default-gateway advertise
!
l2vpn evpn instance 101 vlan-aware
encapsulation vxlan
!
l2vpn evpn instance 201 vlan-aware
encapsulation vxlan
!
interface nve1
no ip address
source-interface Loopback0
host-reachability protocol bgp
member vni 10101 ingress-replication
member vni 20202 ingress-replication
member vni 30303 ingress-replication
member vni 40404 ingress-replication
!
bridge-domain 10
mac aging-time 30
member evpn-instance 101 vni 10101
member GigabitEthernet1 service-instance 10
exit
!
bridge-domain 20
mac aging-time 30
member evpn-instance 101 vni 20202
member GigabitEthernet1 service-instance 20
exit
!
bridge-domain 30
mac aging-time 30
member evpn-instance 201 vni 30303
member GigabitEthernet2 service-instance 30
exit
!
bridge-domain 40
mac aging-time 30
member evpn-instance 201 vni 40404
member GigabitEthernet2 service-instance 40
exit
!
end
!CE-A1
en
!
conf t
!
hostname ce-a1
!
ip routing
!
interface Loopback 0
ip address 10.0.0.1 255.255.255.255
!
interface GigabitEthernet 0/0
no shutdown
!
interface GigabitEthernet 0/0.10
encapsulation dot1Q 10
ip address 1.1.1.1 255.255.255.0
no shutdown
!
interface GigabitEthernet 0/0.20
encapsulation dot1Q 20
ip address 2.2.2.1 255.255.255.0
no shutdown
!
router bgp 65002
neighbor GROUP-A peer-group
neighbor GROUP-A remote-as 65002
neighbor 1.1.1.2 peer-group GROUP-A
neighbor 2.2.2.2 peer-group GROUP-A
no auto-summary
no synchronization
redistribute connected
!
end
!CE-B1
en
!
conf t
!
hostname ce-b1
!
ip routing
!
interface Loopback 0
ip address 10.0.0.2 255.255.255.255
!
interface GigabitEthernet 0/0
no shutdown
!
interface GigabitEthernet 0/0.30
encapsulation dot1Q 30
ip address 1.1.1.1 255.255.255.0
no shutdown
!
interface GigabitEthernet 0/0.40
encapsulation dot1Q 40
ip address 2.2.2.1 255.255.255.0
no shutdown
!
router bgp 65003
neighbor GROUP-B peer-group
neighbor GROUP-B remote-as 65003
neighbor 1.1.1.2 peer-group GROUP-B
neighbor 2.2.2.2 peer-group GROUP-B
no auto-summary
no synchronization
redistribute connected
!
end
!CE-A2
en
!
conf t
!
hostname ce-a2
!
ip routing
!
interface Loopback 0
ip address 10.0.0.3 255.255.255.255
!
interface GigabitEthernet 0/0
no shutdown
!
interface GigabitEthernet 0/0.10
encapsulation dot1Q 10
ip address 1.1.1.2 255.255.255.0
no shutdown
!
interface GigabitEthernet 0/0.20
encapsulation dot1Q 20
ip address 2.2.2.2 255.255.255.0
no shutdown
!
router bgp 65002
neighbor GROUP-A peer-group
neighbor GROUP-A remote-as 65002
neighbor 1.1.1.1 peer-group GROUP-A
neighbor 2.2.2.1 peer-group GROUP-A
no auto-summary
no synchronization
redistribute connected
!
end
!CE-B2
en
!
conf t
!
hostname ce-b2
!
ip routing
!
interface Loopback 0
ip address 10.0.0.4 255.255.255.255
!
interface GigabitEthernet 0/0
no shutdown
!
interface GigabitEthernet 0/0.30
encapsulation dot1Q 30
ip address 1.1.1.2 255.255.255.0
no shutdown
!
interface GigabitEthernet 0/0.40
encapsulation dot1Q 40
ip address 2.2.2.2 255.255.255.0
no shutdown
!
router bgp 65003
neighbor GROUP-B peer-group
neighbor GROUP-B remote-as 65003
neighbor 1.1.1.1 peer-group GROUP-B
neighbor 2.2.2.1 peer-group GROUP-B
no auto-summary
no synchronization
redistribute connected
!
end
!showコマンド結果
ほとんど前回と同じなので今回に関係している部分だけshowコマンドで確認します。
show l2vpn evpn evi detail
PE1
pe1#show l2vpn evpn evi detail
EVPN instance: 101 (VLAN Aware)
RD: 11.11.11.11:101 (auto)
Import-RTs: 65001:101
Export-RTs: 65001:101
Per-EVI Label: none
State: Established
Replication Type: Ingress (global)
Encapsulation: vxlan
IP Local Learn: Enabled (global)
Adv. Def. Gateway: Enabled (global)
Re-originate RT5: Disabled
AR Flood Suppress: Enabled (global)
Bridge Domain: 10
Ethernet-Tag: 10101
State: Established
Flood Suppress: Attached
Core If:
Access If: BDI10
NVE If: nve1
RMAC: 0000.0000.0000
Core BD: 0
L2 VNI: 10101
L3 VNI: 0
VTEP IP: 11.11.11.11
VRF:
IPv4 IRB: Enabled (Asymmetric) ←非対称IRBとして設定されていることが確認できます。
IPv6 IRB: Disabled
Pseudoports:
GigabitEthernet1 service instance 10
Routes: 1 MAC, 1 MAC/IP
Peers:
33.33.33.33
Routes: 2 MAC, 2 MAC/IP, 1 IMET, 0 EAD
Bridge Domain: 20
Ethernet-Tag: 20202
State: Established
Flood Suppress: Attached
Core If:
Access If: BDI20
NVE If: nve1
RMAC: 0000.0000.0000
Core BD: 0
L2 VNI: 20202
L3 VNI: 0
VTEP IP: 11.11.11.11
VRF:
IPv4 IRB: Enabled (Asymmetric)
IPv6 IRB: Disabled
Pseudoports:
GigabitEthernet1 service instance 20
Routes: 1 MAC, 1 MAC/IP
Peers:
33.33.33.33
Routes: 2 MAC, 2 MAC/IP, 1 IMET, 0 EAD
EVPN instance: 201 (VLAN Aware)
RD: 11.11.11.11:201 (auto)
Import-RTs: 65001:201
Export-RTs: 65001:201
Per-EVI Label: none
State: Established
Replication Type: Ingress (global)
Encapsulation: vxlan
IP Local Learn: Enabled (global)
Adv. Def. Gateway: Enabled (global)
Re-originate RT5: Disabled
AR Flood Suppress: Enabled (global)
Bridge Domain: 30
Ethernet-Tag: 30303
State: Established
Flood Suppress: Attached
Core If:
Access If: BDI30
NVE If: nve1
RMAC: 0000.0000.0000
Core BD: 0
L2 VNI: 30303
L3 VNI: 0
VTEP IP: 11.11.11.11
VRF:
IPv4 IRB: Enabled (Asymmetric)
IPv6 IRB: Disabled
Pseudoports:
GigabitEthernet2 service instance 30
Routes: 1 MAC, 1 MAC/IP
Peers:
33.33.33.33
Routes: 2 MAC, 2 MAC/IP, 1 IMET, 0 EAD
Bridge Domain: 40
Ethernet-Tag: 40404
State: Established
Flood Suppress: Attached
Core If:
Access If: BDI40
NVE If: nve1
RMAC: 0000.0000.0000
Core BD: 0
L2 VNI: 40404
L3 VNI: 0
VTEP IP: 11.11.11.11
VRF:
IPv4 IRB: Enabled (Asymmetric)
IPv6 IRB: Disabled
Pseudoports:
GigabitEthernet2 service instance 40
Routes: 1 MAC, 1 MAC/IP
Peers:
33.33.33.33
Routes: 2 MAC, 2 MAC/IP, 1 IMET, 0 EADPE2
pe2#show l2vpn evpn evi detail
EVPN instance: 101 (VLAN Aware)
RD: 33.33.33.33:101 (auto)
Import-RTs: 65001:101
Export-RTs: 65001:101
Per-EVI Label: none
State: Established
Replication Type: Ingress (global)
Encapsulation: vxlan
IP Local Learn: Enabled (global)
Adv. Def. Gateway: Enabled (global)
Re-originate RT5: Disabled
AR Flood Suppress: Enabled (global)
Bridge Domain: 10
Ethernet-Tag: 10101
State: Established
Flood Suppress: Attached
Core If:
Access If: BDI10
NVE If: nve1
RMAC: 0000.0000.0000
Core BD: 0
L2 VNI: 10101
L3 VNI: 0
VTEP IP: 33.33.33.33
VRF:
IPv4 IRB: Enabled (Asymmetric)
IPv6 IRB: Disabled
Pseudoports:
GigabitEthernet1 service instance 10
Routes: 1 MAC, 1 MAC/IP
Peers:
11.11.11.11
Routes: 2 MAC, 2 MAC/IP, 1 IMET, 0 EAD
Bridge Domain: 20
Ethernet-Tag: 20202
State: Established
Flood Suppress: Attached
Core If:
Access If: BDI20
NVE If: nve1
RMAC: 0000.0000.0000
Core BD: 0
L2 VNI: 20202
L3 VNI: 0
VTEP IP: 33.33.33.33
VRF:
IPv4 IRB: Enabled (Asymmetric)
IPv6 IRB: Disabled
Pseudoports:
GigabitEthernet1 service instance 20
Routes: 1 MAC, 1 MAC/IP
Peers:
11.11.11.11
Routes: 2 MAC, 2 MAC/IP, 1 IMET, 0 EAD
EVPN instance: 201 (VLAN Aware)
RD: 33.33.33.33:201 (auto)
Import-RTs: 65001:201
Export-RTs: 65001:201
Per-EVI Label: none
State: Established
Replication Type: Ingress (global)
Encapsulation: vxlan
IP Local Learn: Enabled (global)
Adv. Def. Gateway: Enabled (global)
Re-originate RT5: Disabled
AR Flood Suppress: Enabled (global)
Bridge Domain: 30
Ethernet-Tag: 30303
State: Established
Flood Suppress: Attached
Core If:
Access If: BDI30
NVE If: nve1
RMAC: 0000.0000.0000
Core BD: 0
L2 VNI: 30303
L3 VNI: 0
VTEP IP: 33.33.33.33
VRF:
IPv4 IRB: Enabled (Asymmetric)
IPv6 IRB: Disabled
Pseudoports:
GigabitEthernet2 service instance 30
Routes: 1 MAC, 1 MAC/IP
Peers:
11.11.11.11
Routes: 2 MAC, 2 MAC/IP, 1 IMET, 0 EAD
Bridge Domain: 40
Ethernet-Tag: 40404
State: Established
Flood Suppress: Attached
Core If:
Access If: BDI40
NVE If: nve1
RMAC: 0000.0000.0000
Core BD: 0
L2 VNI: 40404
L3 VNI: 0
VTEP IP: 33.33.33.33
VRF:
IPv4 IRB: Enabled (Asymmetric)
IPv6 IRB: Disabled
Pseudoports:
GigabitEthernet2 service instance 40
Routes: 1 MAC, 1 MAC/IP
Peers:
11.11.11.11
Routes: 2 MAC, 2 MAC/IP, 1 IMET, 0 EADshow l2route evpn default-gateway
PE1
pe1#show l2route evpn default-gateway
EVI ETag Prod Mac Address Host IP Next Hop(s)
----- ---------- ----- -------------- --------------------------------------- --------------------------------------------------
101 10101 BGP 0000.0000.0010 1.1.1.254 V:10101 33.33.33.33
101 10101 L2VPN 0000.0000.0010 1.1.1.254 BD10:0
101 20202 BGP 0000.0000.0020 2.2.2.254 V:20202 33.33.33.33
101 20202 L2VPN 0000.0000.0020 2.2.2.254 BD20:0
201 30303 BGP 0000.0000.0030 1.1.1.254 V:30303 33.33.33.33
201 30303 L2VPN 0000.0000.0030 1.1.1.254 BD30:0
201 40404 BGP 0000.0000.0040 2.2.2.254 V:40404 33.33.33.33
201 40404 L2VPN 0000.0000.0040 2.2.2.254 BD40:0PE2
pe2#show l2route evpn default-gateway
EVI ETag Prod Mac Address Host IP Next Hop(s)
----- ---------- ----- -------------- --------------------------------------- --------------------------------------------------
101 10101 BGP 0000.0000.0010 1.1.1.254 V:10101 11.11.11.11
101 10101 L2VPN 0000.0000.0010 1.1.1.254 BD10:0
101 20202 BGP 0000.0000.0020 2.2.2.254 V:20202 11.11.11.11
101 20202 L2VPN 0000.0000.0020 2.2.2.254 BD20:0
201 30303 BGP 0000.0000.0030 1.1.1.254 V:30303 11.11.11.11
201 30303 L2VPN 0000.0000.0030 1.1.1.254 BD30:0
201 40404 BGP 0000.0000.0040 2.2.2.254 V:40404 11.11.11.11
201 40404 L2VPN 0000.0000.0040 2.2.2.254 BD40:0show l2route evpn mac ip
PE1
pe1#show l2route evpn mac ip
EVI ETag Prod Mac Address Host IP Next Hop(s)
----- ---------- ----- -------------- --------------------------------------- --------------------------------------------------
101 10101 BGP 0000.0000.0010 1.1.1.254 V:10101 33.33.33.33
101 10101 L2VPN 0000.0000.0010 1.1.1.254 BD10:0
101 10101 L2VPN 5254.0004.9f62 1.1.1.1 Gi1:10
101 10101 BGP 5254.000b.b606 1.1.1.2 V:10101 33.33.33.33
101 20202 BGP 0000.0000.0020 2.2.2.254 V:20202 33.33.33.33
101 20202 L2VPN 0000.0000.0020 2.2.2.254 BD20:0
101 20202 L2VPN 5254.0004.9f62 2.2.2.1 Gi1:20
101 20202 BGP 5254.000b.b606 2.2.2.2 V:20202 33.33.33.33
201 30303 BGP 0000.0000.0030 1.1.1.254 V:30303 33.33.33.33
201 30303 L2VPN 0000.0000.0030 1.1.1.254 BD30:0
201 30303 L2VPN 5254.0009.6777 1.1.1.1 Gi2:30
201 30303 BGP 5254.0019.c5ca 1.1.1.2 V:30303 33.33.33.33
201 40404 BGP 0000.0000.0040 2.2.2.254 V:40404 33.33.33.33
201 40404 L2VPN 0000.0000.0040 2.2.2.254 BD40:0
201 40404 L2VPN 5254.0009.6777 2.2.2.1 Gi2:40
201 40404 BGP 5254.0019.c5ca 2.2.2.2 V:40404 33.33.33.33PE2
pe2#show l2route evpn mac ip
EVI ETag Prod Mac Address Host IP Next Hop(s)
----- ---------- ----- -------------- --------------------------------------- --------------------------------------------------
101 10101 BGP 0000.0000.0010 1.1.1.254 V:10101 11.11.11.11
101 10101 L2VPN 0000.0000.0010 1.1.1.254 BD10:0
101 10101 BGP 5254.0004.9f62 1.1.1.1 V:10101 11.11.11.11
101 10101 L2VPN 5254.000b.b606 1.1.1.2 Gi1:10
101 20202 BGP 0000.0000.0020 2.2.2.254 V:20202 11.11.11.11
101 20202 L2VPN 0000.0000.0020 2.2.2.254 BD20:0
101 20202 BGP 5254.0004.9f62 2.2.2.1 V:20202 11.11.11.11
101 20202 L2VPN 5254.000b.b606 2.2.2.2 Gi1:20
201 30303 BGP 0000.0000.0030 1.1.1.254 V:30303 11.11.11.11
201 30303 L2VPN 0000.0000.0030 1.1.1.254 BD30:0
201 30303 BGP 5254.0009.6777 1.1.1.1 V:30303 11.11.11.11
201 30303 L2VPN 5254.0019.c5ca 1.1.1.2 Gi2:30
201 40404 BGP 0000.0000.0040 2.2.2.254 V:40404 11.11.11.11
201 40404 L2VPN 0000.0000.0040 2.2.2.254 BD40:0
201 40404 BGP 5254.0009.6777 2.2.2.1 V:40404 11.11.11.11
201 40404 L2VPN 5254.0019.c5ca 2.2.2.2 Gi2:40疎通確認
こちらも今回設定追加したIRBへの疎通ができるかどうかだけ確認します。
ping
CE-A1
ce-a1#ping 1.1.1.254
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 1.1.1.254, timeout is 2 seconds:
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 1/1/1 ms
ce-a1#ping 2.2.2.254
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 2.2.2.254, timeout is 2 seconds:
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 1/1/1 msCE-B1
ce-b1#ping 1.1.1.254
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 1.1.1.254, timeout is 2 seconds:
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 1/1/1 ms
ce-b1#ping 2.2.2.254
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 2.2.2.254, timeout is 2 seconds:
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 1/1/1 msCE-A2
ce-a2#ping 1.1.1.254
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 1.1.1.254, timeout is 2 seconds:
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 1/1/2 ms
ce-a2#ping 2.2.2.254
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 2.2.2.254, timeout is 2 seconds:
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 1/1/1 msCE-B2
ce-b2#ping 1.1.1.254
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 1.1.1.254, timeout is 2 seconds:
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 1/1/1 ms
ce-b2#ping 2.2.2.254
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 2.2.2.254, timeout is 2 seconds:
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 1/1/1 msということでIRBへの疎通は問題なくできていそうです。
ちなみにCE-A1のARP確認結果はこんな感じでIRBは手動登録したMACアドレスが登録されています。
ce-a1#show arp
Protocol Address Age (min) Hardware Addr Type Interface
Internet 1.1.1.1 - 5254.0004.9f62 ARPA GigabitEthernet0/0.10
Internet 1.1.1.2 85 5254.000b.b606 ARPA GigabitEthernet0/0.10
Internet 1.1.1.254 0 0000.0000.0010 ARPA GigabitEthernet0/0.10
Internet 2.2.2.1 - 5254.0004.9f62 ARPA GigabitEthernet0/0.20
Internet 2.2.2.2 85 5254.000b.b606 ARPA GigabitEthernet0/0.20
Internet 2.2.2.254 0 0000.0000.0020 ARPA GigabitEthernet0/0.20前回の課題解決と新たな課題
- 分散型の非対称IRBの設定がうまくいったことにより、cat8000vでは集中型のIRBはできない(?)ものの分散型の非対称IRBであれば設定可能ということが分かった。
- 以前、cat9000vでvlan-basedの集中型の非対称IRBを実施した際もそうだが、IOS-XEでL2VPNルートとIPv4 VRFルート間のルートリーク(再配送?)ができていないため、現状L2VPN内でデフォルトGWの設定を行ったところであまり意味がない。
- 分散型Anycast-Gatewayでは同一BD内で同じIPアドレスを持つが、このIPアドレスをピアとしたBGPピアを設定した際、物理的にはインターフェースが二つあるのが原因でCE-A1はPE1にピアを張り、CE-A2はPE2にピアを張ってしまうので、BGPの中継がうまくいかない。おそらくこれもL2VPNルートとIPv4 VRFルート間のルートリークができれば解決すると思われる。
後書き
IOS-XEでのEVPN-VXLANは行き詰った感じがあるので、いったん一区切りつけて別の検証を行おうと思います。
つよつよエンジニアが道を切り開いてくださることを願って…🙄
脚注
- 以下の13スライド目
https://www.nic.ad.jp/ja/materials/iw/2016/proceedings/t05/t5-kamitani-2.pdf ↩︎ - Ciscoのドキュメント
https://www.cisco.com/c/en/us/td/docs/switches/lan/catalyst9600/software/release/17-3/configuration_guide/vxlan/b_173_bgp_evpn_vxlan_9600_cg/configuring_evpn_vxlan_integrated_routing_and_bridging.html#:~:text=Manual%20MAC%20address%20configuration%20and%20MAC%20aliasing%20are%20the%20two%20methods%20used%20to%20maintain%20the%20same%20MAC%20address%20across%20all%20VTEPs%20and%20configure%20distributed%20anycast%20gateway. ↩︎ - Ciscoのコミュニティ情報
https://community.cisco.com/t5/routing/vxlan-questions/td-p/5202207#:~:text=on%20IOS%20XE%20you%20can%20use%20the ↩︎ - 過去の記事
https://enjimiya.com/vrfbgpvlan%e3%81%ab%e3%82%88%e3%82%8b%e3%83%88%e3%83%a9%e3%83%95%e3%82%a3%e3%83%83%e3%82%af%e3%81%ae%e8%ab%96%e7%90%86%e5%88%86%e5%89%b2/#:~:text=%E3%81%A9%E3%81%86%E3%82%84%E3%82%89CML%E3%81%AE%E3%83%87%E3%83%95%E3%82%A9%E3%83%AB%E3%83%88%E3%81%AE%E3%83%A9%E3%82%A4%E3%82%BB%E3%83%B3%E3%82%B9%E3%81%A0%E3%81%A8%E3%80%81cat9000v%E3%81%A7%E3%81%AFVRF%E3%81%AA%E3%81%A9%E3%81%8C%E4%BD%BF%E3%81%88%E3%81%AA%E3%81%841%E3%82%88%E3%81%86%E3%81%AA%E3%81%AE%E3%81%A7%E3%80%81%E3%81%BE%E3%81%9A%E3%82%A2%E3%83%89%E3%83%90%E3%83%B3%E3%83%86%E3%83%BC%E3%82%B8%E3%83%A9%E3%82%A4%E3%82%BB%E3%83%B3%E3%82%B9%E3%81%AE%E6%9C%89%E5%8A%B9%E5%8C%96%E3%82%92%E8%A1%8C%E3%81%84%E3%81%BE%E3%81%99%E3%80%82 ↩︎

コメント